Md4 Hash Cracker
8 August 2020
Woodpecker hash Bruteforce, also known as Hash bruteforce, is a very fast and powerful multithreaded hash cracker (brute-forcer) with many features including 4 attack types, session pausing and restoring, saving results to a file and much more. MDcrack is a an aggressive cracker for MD2 MD4 MD5 HMAC-MD4 HMAC-MD5 NTLM PIX IOS APACHE FREEBSD hashes. The first hash after the username is a Lanmanager hash. It can be run against various encrypted password formats including several crypt password hash types most commonly found on various Unix flavors (based on DES, MD5, or Blowfish), Kerberos AFS, and Windows NT/2000/XP/2003 LM hash. H The type of hash NTLM MD5 and MD4 are currently supported-c The charset we want to use. The is a complete list inside the charset directory.-f the path to the file where we have our hash. We can add as many hash’s to the file as we want. –min= minimum number of chars to try –max= maximum number of char to try. The limit for NTLM is 14. Ntlm is an authentification protocol created by Microsoft. This function is used for a lot of different applications and is based on cryptographic function Md4, with few differencies. Ntlm is often used to encrypt Windows users passwords.
Md4 Hash Cracker
4 minutes to readToday I was stumbled across a hacking challenge website called tryhackme. Multiple challenges can be found and each of the challenges is written by the community or individual. Feel free to sign up yourself and take part the challenges.
Long story short, I will guide you on the challenge named crackthehash. This challenge is extremely easy if you are an experienced hacker/code cracker. The challenge consists of 9 tasks and I will explain it one by one.
Task 1-1: MD5 hash
This one is easy, there are two ways to crack this MD5 hash
Md4 Hash Cracker Game
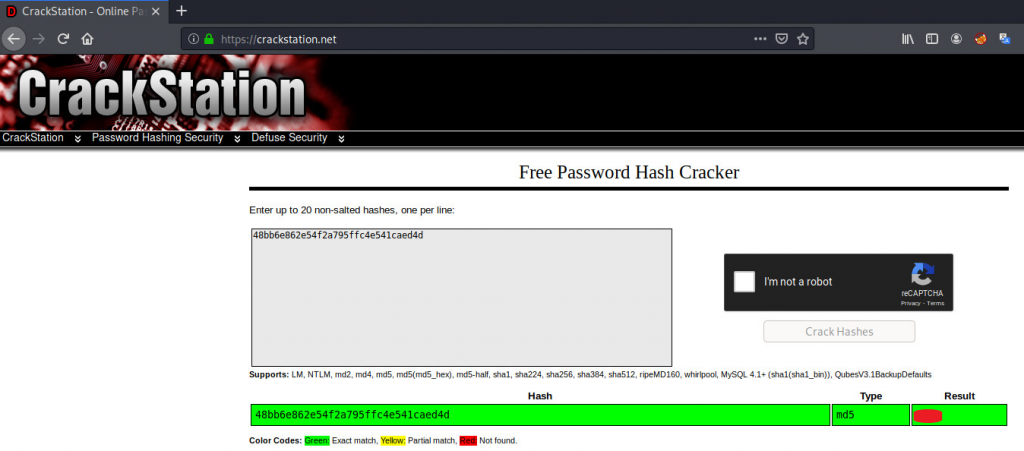
Method 1: Online hash cracker
You can visit any hash cracker site to crack the hash instantly. For example, the crack station. Just paste the hash and crack it.
Method 2: Hashcat
This method is more flexible when compared to the online hash cracker. It provides a tons of hash mode. You can download hashcat (Window/Linux/MacOS) from this website. However, you need to know some command line for terminal/CMD as the prerequisite of using this tool. On the other hand, I highly recommend launching this tool in your host computer (not on your virtual machine). This is due to cracking the hash require a large amount of processing resource and GPU is the ideal choice when compared to CPU. Also, the virtual machine cannot access GPU resource.
For this walk-through, I’m going to use Window OS. After you have downloaded the hashcat, be sure to redirect to the path where you extract the hashcat (using the command: cd). Also, I going to use dictionary attack for this hash crack walk-through, you can download the famous wordlist (rockyou.txt). After that, I store the rockyou.txt into the ‘Dict’ directory (the directory is inside the hashcat folder).
Please create a ‘Hash’ directory to store all the hashes that going to be cracked soon. For this case, i saved my hash in ‘hash.txt’.
After that launch the hashcat using following command
- hashcat64.exe –> hashcat run in 64bit
- -D –> choosing the processor mode (1-CPU, 2-GPU 3-FPGA)
- -m –> Hash mode (0-MD5), please refer to hashcat mode
After a few second/minute, the result shows in the terminal.
Task 1-2: SHA1 hash
Similar to Task 1-1, but the mode is (-m 100) for hashcat
Task 1-3: SHA256 hash
Similar to Task 1-1, but the mode is (-m 1400) for hashcat
Task 1-4: bcrypt-blowfish hash
This one is little bit tricky which is this hash cannot be cracked using online tool. That is why hashcat came in, set the mode to -m 3200
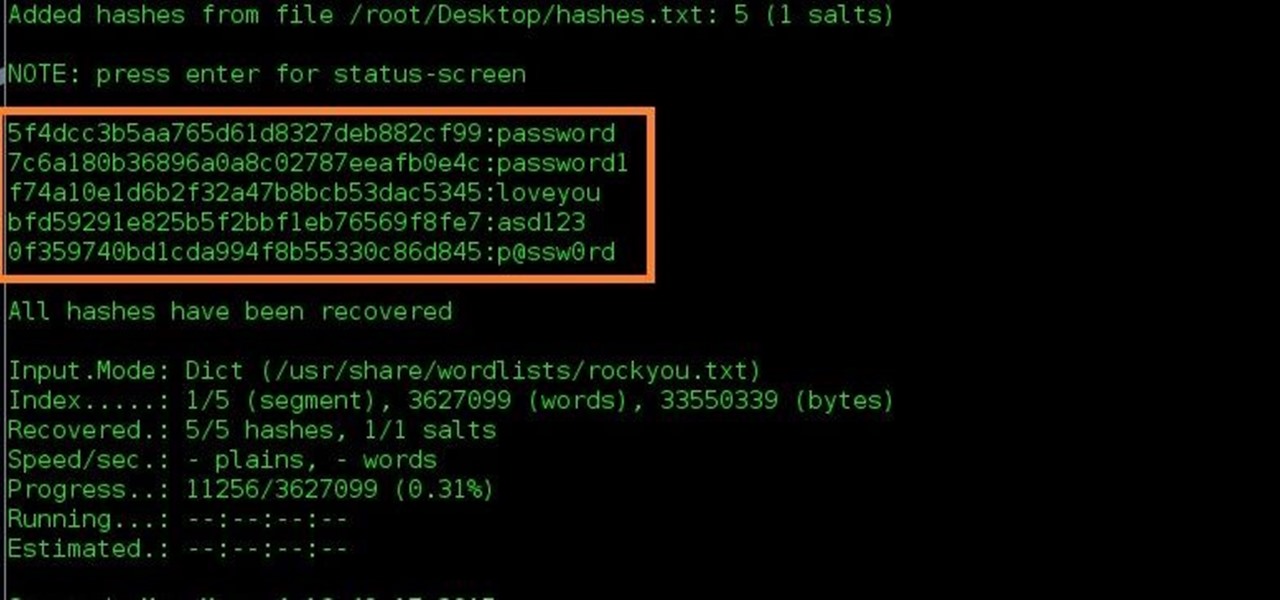
Task 1-5: MD4 hash
Similar to Task 1-1, but the mode is (-m 900) for hashcat
Task 2-1: SHA256 hash
Similar to Task 1-1, but the mode is (-m 1400) for hashcat
Task 2-2: NTLM hash
Similar to Task 1-1, but the mode is (-m 1000) for hashcat
Task 2-3: SHA512crypt, $6$ hash
This hash cannot be cracked using online tool but can be cracked using hashcat by setting the mode -m 1800. (It take some time).
Task 2-4: SHA1 with salt hash
This hash also cannot be cracked using online tool due to the present of salt ( tryhackme ). This only can be done by using hashcat with mode -m 110.
Identify hash
If you were not sure what kind of hash is presented on your monitor, you can try to detect the hash. It listed out all possible hashes.
Conclusion
Cracking hashes are fun and challenge. Be sure the share this post. and have a nice day :)
tags: tryhackme - hash - crackThanks for reading. Follow my twitter for latest update
If you like this post, consider a small donation. Much appreciated. :)
Vortex
Other algorithms calculators
MD2MD4MD5SHA1SHA224SHA256SHA384SHA512/224SHA512/256SHA512SHA3-224SHA3-256SHA3-384SHA3-512RIPEMD128RIPEMD160RIPEMD256RIPEMD320WHIRLPOOLTIGER128,3TIGER160,3TIGER192,3TIGER128,4TIGER160,4TIGER192,4SNEFRUSNEFRU256GOSTGOST-CRYPTOADLER32CRC32CRC32BFNV132FNV1A32FNV164FNV1A64JOAATHAVAL128,3HAVAL160,3HAVAL192,3HAVAL224,3HAVAL256,3HAVAL128,4HAVAL160,4HAVAL192,4HAVAL224,4HAVAL256,4HAVAL128,5HAVAL160,5HAVAL192,5HAVAL224,5HAVAL256,5Usage FAQ
Usage from Address Bar
You can use direct access to this page from your browser address bar. Type string that you need to encode with algorithm according to next schema: https://md5calc.com/hash/<ALGORITHM>/<PHRASE> For example to visit page that contains hash of 'hello world' you can just visit url: https://md5calc.com/hash/md5/hello+world The another cool thing is that you can specify 'json' or 'plain' mode into URL and you will get only HASH in response. Schema of this future: https://md5calc.com/hash/<ALGORITHM>.<OUTPUT:plain|json>/<PHRASE> Example: https://md5calc.com/hash/md5.json/hello+world Will output only: '5eb63bbbe01eeed093cb22bb8f5acdc3'
If you have string that contains complicated urlencoded characters you can send it directly via params to avoid processing of our url parser. Use:
str - for string to encode
algo - for algorithm
output - for output type (empty, 'json' or 'plain')https://md5calc.com/hash?algo=<ALGORITHM>&str=<PHRASE>&output=<OUTPUT:plain|json>https://md5calc.com/hash?algo=md5&str=hello%0Aworldhttps://md5calc.com/hash/md5?str=hello%0Aworld
Usage from Javascript
We have removed CORS restriction so you can use direct access to hash calculator in your javascript applications via AJAX.
Example: Will output: JSON of 'hello world' is '5eb63bbbe01eeed093cb22bb8f5acdc3'
Usage from PHP
You can use direct access to hash in your applications.
PHP Example: <?php Will output:
$str = 'hello world';
$url ='https://md5calc.com/hash/md5.plain/'.urlencode($str);
$md5hash = file_get_contents($url);
echo 'Hash of '.$str.' is '.$md5hash.''; Hash of 'hello world' is '5eb63bbbe01eeed093cb22bb8f5acdc3'
Keep in mind that this example no make sense because PHP has builtin function hash() which do the same.
Chains of algorithms
In some cases you can need encode string with two or more algorithms. For these cases we have introduced chains of algorithms. For example if you need to encode string according to this schema md5(sha512(sha1('hello world'))) you can do this by connecting algorithms with a double dash: https://md5calc.com/hash/md5--sha512--sha1/hello+world If you will do this in your address bar you can also use semicolon instead of double dash. https://md5calc.com/hash/md5;sha512;sha1/hello+world Pay attention that semicolon should be encoded in url, so if you use it not in your browser, you should use '%3B' instead https://md5calc.com/hash/md5%3Bsha512%3Bsha1/hello+world Such approach can be also used with 'plain' and 'json' mode https://md5calc.com/hash/md5--sha512--sha1.plain/hello+worldhttps://md5calc.com/hash/md5;sha512;sha1.json/hello+world
You can also use special chain item 'b64d' or 'base64decode' to make base64 decode. It can help to hash any of not printable characters. Example: https://md5calc.com/hash/md5.plain/hello+worldhttps://md5calc.com/hash/b64d--md5.plain/aGVsbG8gd29ybGQ= will be the same: 5eb63bbbe01eeed093cb22bb8f5acdc3
At present time you can use it only through url..
Carriage Return and Line Feed characters
At present time our text editor doesn't have functionality that can take into account which of those characters you want to keep in string. This problem come from browsers which normalize all of the line endings to 'CRLF' ('rn') format according to 'HTML specification'. It means that if you paste from buffer string'hellonword' and press 'Encode', your browser will convert it to 'hellornword' and only after this your browser send FORM to us. As a result we will show you hash of 'hellornword' but not 'hellonword'
You can avoid this with encode string to 'base64' on your side and use 'Chains of algorithms' that described above.
Example 1: Hash from string with only Line Feed (LF) character Text: hellonworld
Text encoded to BASE64: aGVsbG8Kd29ybGQ=
URL: https://md5calc.com/hash/b64d--md5.plain/aGVsbG8Kd29ybGQ=
RESULT: 9195d0beb2a889e1be05ed6bb1954837
Example 2: Hash from string with Carriage Return (CR) and Line Feed (LF) character. This result you will have if you use editor with CR, LF or CRLF symbols. Text: hellornworld
Text encoded to BASE64: aGVsbG8NCndvcmxk
URL: https://md5calc.com/hash/b64d--md5.plain/aGVsbG8NCndvcmxk
RESULT: 6a4316b18e6162cf9fcfa435c8eb74c1