Decrypt Keychain.plist
Part 1 of this series may be found here.
Part 2 of this series may be found here.
Part 3 of this series may be found here.
Part 4 of this series may be found here.

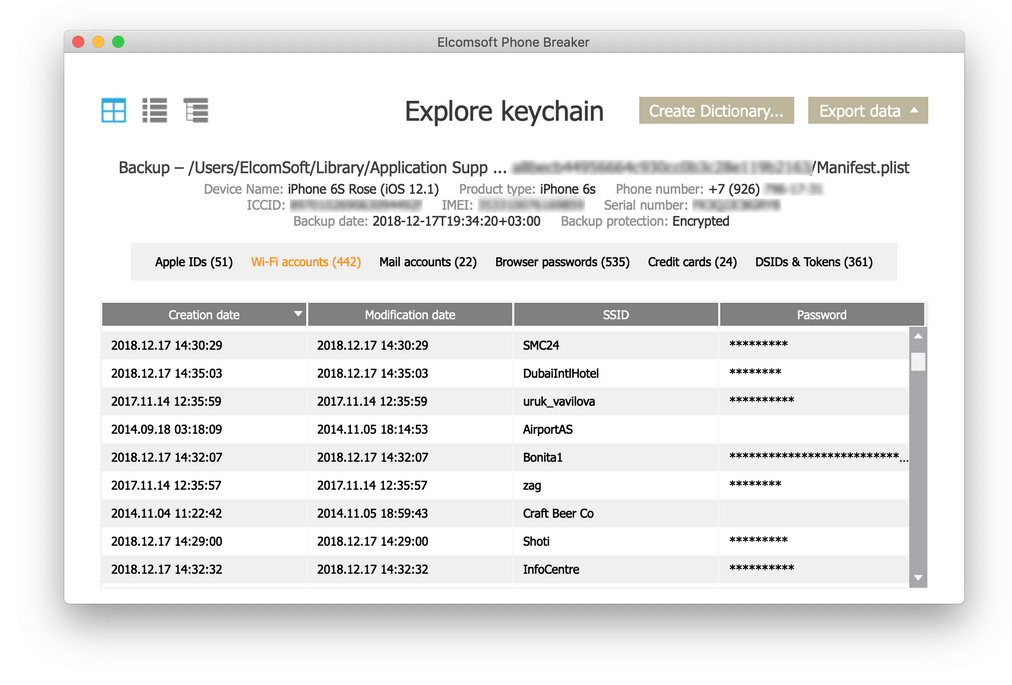
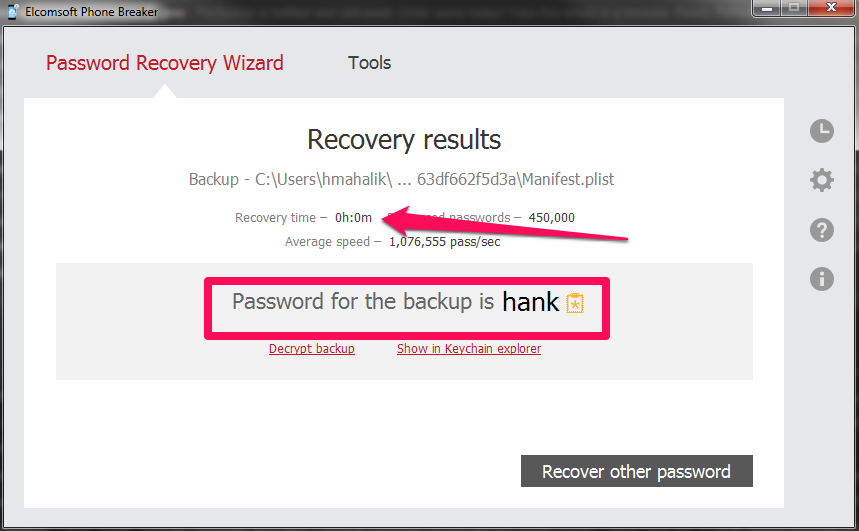
EPB is able to decrypt keychain data from password-protected backups (iOS 4 and later) if the backup password is known (or has been recovered using EPB for Windows). For iTunes backups that do not have the password set, as well as for iCloud backups, keychain can be decrypted only if. Encryption keys / certificates. The importance of being able to access such information needs little elaboration but, that said, examination of keychain data may also be useful to identify passwords that may have been re-used for other purposes; also passwords that share a common theme, such as names of pets, family members or members of a. Aug 05, 2020 In order to unwrap the encryption key, the correct passcode must be provided. While it’s incredibly easy for Apple to build a piece of software allowing the company to brute-force the passcodes, unwrap the encryption key and decrypt the keychain, the company publicly refuses to do so. This site contains user submitted content, comments and opinions and is for informational purposes only. Apple may provide or recommend responses as a possible solution based on the information provided; every potential issue may involve several factors not detailed in the conversations captured in an electronic forum and Apple can therefore provide no guarantee as to the.
Encryption algorithm. Encrypted data stored on the disk is decrypted on the fly when requested from an authentication device. Data stored on the iCloud can also be backed up to a computer. Detailed procedure is available at Apple documentation. On the iPhone, iCloud backup storage can be turned on/off by navigating to Settings - iCloud.
Safari
I must admit, I was pretty surprised by how hidden Apple made their security information. After years of hearing how horrible Safari is in terms of general security – their password security is actually pretty decent. unfortunately, it too is able to be hacked if you know what you’re doing.
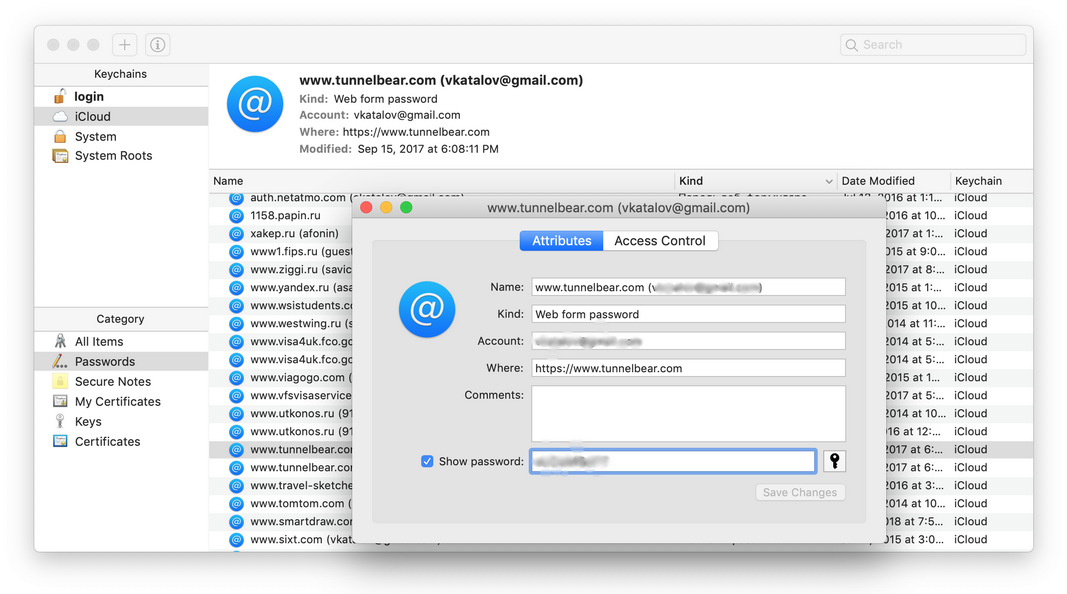
Safari stores your usernames and passwords in a file called “keychain.plist” in the following folders:
Sorry Mac users, I don’t know where this is stored on a Mac… If someone wants to give me a Mac, I’ll be more than happy to research it for them… 🙂
The contents of this file are pseudo-encrypted because it’s stored in a “Binary Property List” file format which is an Apple format for storing binary data. If you just open the file it will look like garbage. However, Apple provides a tool called plutil.exe that can read this format and it’s actually provided with Safari in the following folders:
Run this program in DOS using the following commands:
This will convert the .plist file into an XML file. In the XML file, everything will be decoded except for your password which will be inside an tag called
The encrypted password is encoded using the BASE64 algorithm. Bizarrely enough, the original password data stored in the keychain.plist file is not encoded with BASE64. It is only encrypted to BASE64 when converting the .plist file into XML using the plutil program. In the .plist file, the password is encrypted using standard Windows Data Protection (DPAPI), which provides the known functions of CryptProtectData and CryptUnprotectData for encrypting / decrypting of data using your Windows authentication password. When using CryptProtectData, Safari uses a standard, static salt for all passwords which is also stored in the keychain.plist file.
So to actually decode the XML file, you must first decrypt the BASE64 encrypted data, then decrypt the Windows DPAPI encrypted data. Easy right?
BASE64 encryption can easily be broken with free code available online. From there, you need to figure out the salt to use with the Windows DPAPI CryptUnprotectData function.
For the curious, the salt generation algorithm and decryption functions are available in the Apple supplied CFNetwork.dll file which can be found in the following folders:
Decrypt Keychain.plist Iphone
The salt data in the .plist file is 144 bytes long and ends with “com.apple.Safari”. Once you find the Salt in the .plist file, you can easily decrypt the passwords using the CryptUnprotectData function (available on the Microsoft MSDN website).
Decrypt Keychain.plist Codes
As you can see, Safari is much more complicated than other browsers but in the end, it’s just as easy for someone who knows what they are doing to hack.
Summary
Decrypt Keychain.plist Password
I think that all the browsers fall short in one area or another. Firefox comes the closest but only if you enable a Master Password. IE9 has good security for Autocomplete data, but only if you do not store website history. Chrome fails in terms of protecting your usernames and passwords from any key loggers. Opera fails completely because it uses a known, static salt. Safari surprisingly enough provides decent security from someone who doesn’t know what they are doing but a true hacker should be able to decrypt your passwords with some patience.
Decrypt Keychain.plist Email
My recommendation? Use Firefox, keep it updated and enable a strong Master Password. Again, I refer you to check out XKCD’s Password Strength cartoon for tips.